Tutorial Rootkits: Part-1
What are rootkits?
As the name
specifies it’s a combination of two words root and kit. Root defines
administrative name onUNIX and Linux operating system and in windows its
administrative access and kit refers to a bunch of programs.
So Rootkit
is a collection of tools that enables Administrative level access to a computer
or computer network. Tools may be key logger, spyware, Backdoor, downloader
etc. it can be anything which can take benefit of the vulnerability and exploit
the user (victim).
A rootkit is
a type of malicious software that is activated every time your system boots up
and penetrates Windows API’s.
Behavior of Rootkits
A rootkit
allows hacker to establish a command and control server on the victim’s machine
without the user knowing about it. Once it is installed the hacker can remotely
access user’s machine and change system configuration on the user’s machine and
do anything on the victim’s machine.
Basic Analysis of Root kits
This
kind of virus is not easily be removed as it sneaks in the deepest of computer
system and inserts the hidden malcode in certain folders that can't be detected
by Anti Virus tools. It can even disable applications like malware bytes,
tdsskiller etc.
There are
several kind of rootkits here we are going to analyze a type which hides its
functionality and all the hidden files are stored in the system. To view we
need to first change settings in Folder and Search options as follows:
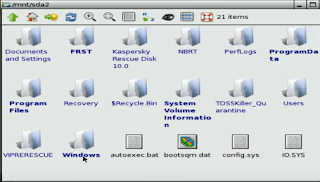
Now you will
find any hidden folder here the sample having folder name Installer C:\Windows\Installer
There is one
other hidden folder which seems interesting and is a root kit.
Even if you
try to delete this file you will not be able to do it even you can see that
date modified is also old and even if you want to rename it you can’t do it.
This folder
contains some folders and system files as
What this
folder contains and what it’s basically doing
· It’s
disabling all the antivirus and anti malware programs.
· Inability
to access registry Editor.
· Inability
to access application.
· Creates
a”backdoor” to steal your personal information, including banking passwords Etc.
Now go to
location C:\Users\Default\AppData\Local you will find the same hidden folder which
is a rootkit and having only one sys file which is stopping us to running
anything.
This is all
about where it actually resides and what its doing as we seen that I already
explained that we were not able to delete that file.
So now
question is How to remove this virus?
Removal of Rootkit Malware
There are
several ways of removing it Here we are using here is Puppy Linux which is a
free ware you can download it easily and now first
1. We will restart our system and we
will boot puppy linux and will mount our Windows sytem as follows
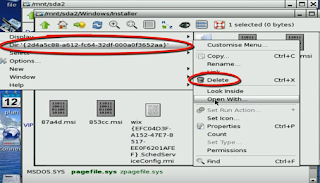
Here you can see the Windows folder
which is the same where the hidden Installer folder resides.
2. Now will go to same folder and same
file we have seen their where actually the virus resides
3. Now we are going to delete this file
just right click on that you will find Dir and folder name just move the cursor
on it you will get a delete option.
4. Click on delete and remember one
thing while deleting you have to check the force checkbox which will come once
you click on delete.
5. Now go to the users path and delete
folder from there as well.
6. Now your rootkit has been deleted.
For more
like what that rootkit doing what registry entries that is changing wait for
Part 2





No comments:
Post a Comment