Macro Malware Hits Mac Users
After hounding Windows users, macro malware has taken its first steps towards affecting the other operating system on which the Microsoft Office suite is available, and that's Apple's macOS.
One of the first macro malware attacks on macOS users was discovered this week, on Monday, by Snorre Fagerland, Senior Principal Security Researcher at Symantec, and later analyzed by Patrick Wardle, Director of Research at Synack.
The file in question was a word file named "U.S. Allies and Rivals Digest Trump's Victory - Carnegie Endowment for International Peace.docm," which at the time it was discovered, was only detected by four antivirus scanners on VirusTotal.
According to Wardle, this Word document contained a macro script that prompted Office to show Mac users a warning that most Windows users are very familiar with.
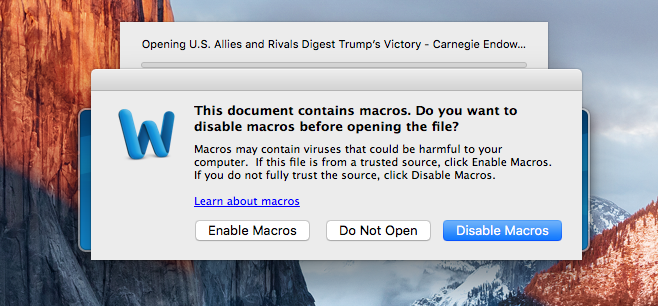
Allowing the macro scripts to execute when opening the Word file would result in an immediate infection, as the malicious code contained within was set to execute under an auto-open function.
Wardle, who extracted the macro script and analyzed it, says the macro contained a chunk of base64 data, which it extracted and executed as Python commands.
After a closer look at these commands, Wardle says the script would go through four stages:
- Check if a Mac security app called LittleSnitch was running
- Downloads another payload from a remote server (https://www.securitychecking.org:443/index.asp)
- Decrypts the payload via RC4
- Execute the decrypted payload
Because the remote server was down when Wardle analyzed the macro script, he never got to verify the true capabilities and purpose of the second-stage payload.
Nevertheless, Wardle did identify the commands in the first-stage payload as snippets taken from EmPyre, a post-exploitation OS X/Linux agent written in Python 2.7.
Common sense says that the second-stage payload must have also borrowed some tricks from EmPyre, which includes modules for dumping the Apple keychain (password store), spying via the webcam, and stealing browser history files.
Wardle also discovered that the server from where the Word macro script downloaded the second-stage payload was located in Russia, on an IP address previously associated with other malware campaigns.
"Overall this malware sample isn't particularly advanced. [...] However let's be nice and give the attackers some credit," Wardle says. "By using a macros in Word [sic] document they are exploiting the weakest link; humans! And moreover since macros are 'legitimate' functionality (vs. say a memory corruption vulnerability) the malware's infection vector doesn't have to worry about crashing the system nor being 'patched' out."
Mac malware isn't as rare as it once was
In the past years, Mac users have been generally ignored by malware authors, similarly to Linux users. Nonetheless, attacks on both Mac and Linux users are now intensifying as both operating systems have become more popular.
On the same day the macro malware attack targeting Mac users was discovered, Claudio Guarnieri, security researcher for Citizen Lab, published research on an Iranian APT called iKittens, who developed and deployed a new Mac malware called MacDownloader.

No comments:
Post a Comment